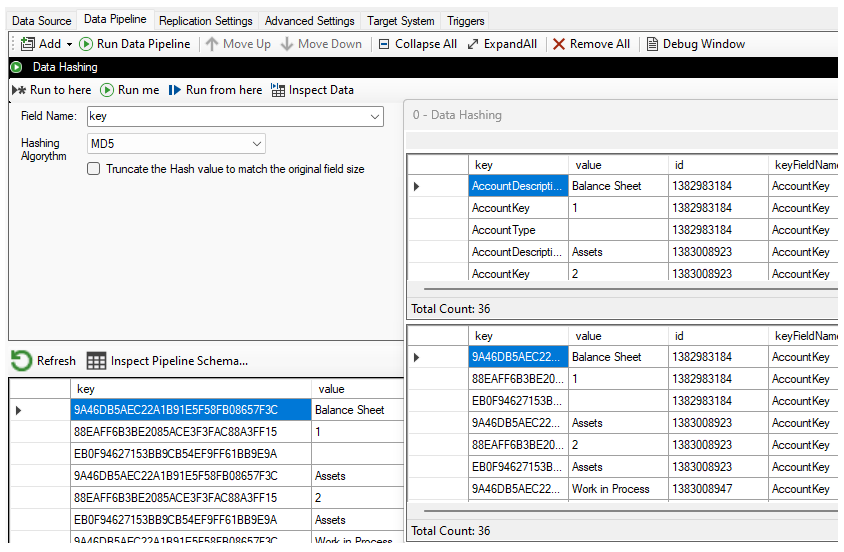
Data Hashing
This component allows you to mask sensitive data on the fly by applying a hashing operation on a field. One of the advantages of hashing (as compared to masking) is that while the values cannot be reversed-engineered, two identical values will have the same hash value. The following Hash algorythms are available:
- MD5
- SHA1
- SHA256
- SHA384
- SHA512
Example
In this example, the MD5 operation is applied on the first field.