X.509 Certificates
DataZen allows you to store X.509 certificates for encryption and signature.
Certificates and Connection Strings are stored inside DataZen and are encrypted using AES.
| Usage | Storage | Comments |
|---|---|---|
| HTTP/S Connections | connection string | These certificates are stored encrypted directly as part of the connection string table |
| Change Logs | certificate store | These certificates are stored in an encrypted certificate table in DataZen or on the localhost depending on the agent |
Cloud agents do not offer a localhost store for Change Log certificates; all certificates are stored encrypted in the DataZen database.
Connection strings and certificates are encrypted in the DataZen database using AES and a default key encryption key (KEK). You can change the KEK from DataZen Manager at any time; once changed, you cannot revert to the default KEK.
X.509 Certs for HTTP/S Connections
Some HTTP/S endpoints require the use of a X.509 certificate for enhanced security; for example, connecting to ADP require using a certificate. When using a certificate for this purpose, the certificate itself is loaded and saved in its entirety as part of the connection string in DataZen.
When you Copy and Paste connection strings, the full connection is copied in memory including any certificate.
For more information about HTTP/S settings see X.509 Certificates in the HTTP/S section.
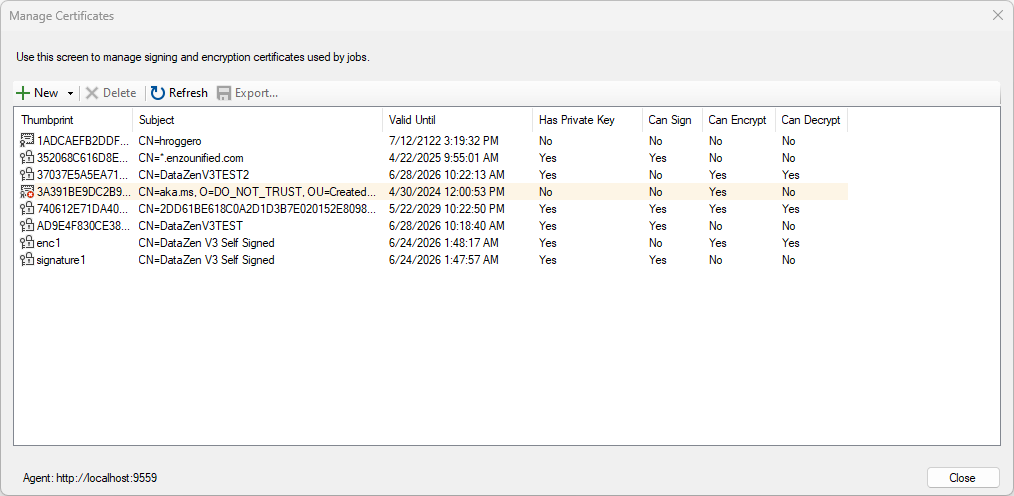
Registering X.509 Certificates
To manage X.509 certificates for Change Logs, or to use signing certificates for signing or authentication purposes,
go to Configuration -> Security -> Manage Certificates... in DataZen Manager.
You can manage encryption, decryption, and signing certificates from here.
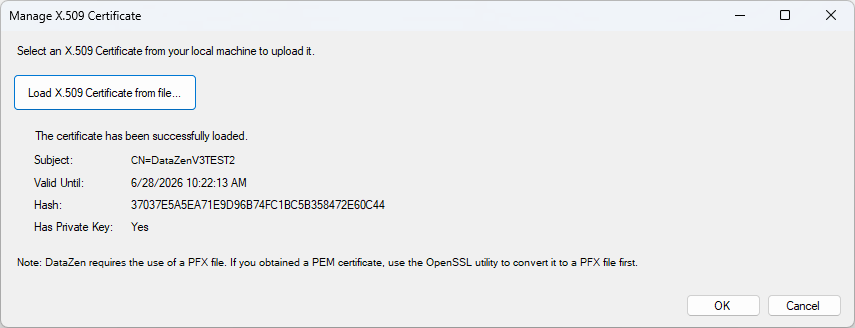
Import a PFX Certificate
To import an existing PFX certificate from disk, choose New -> Import PFX From File and select your certificate.
If the certificate is encrypted with a password, you will be prompted to enter it then.
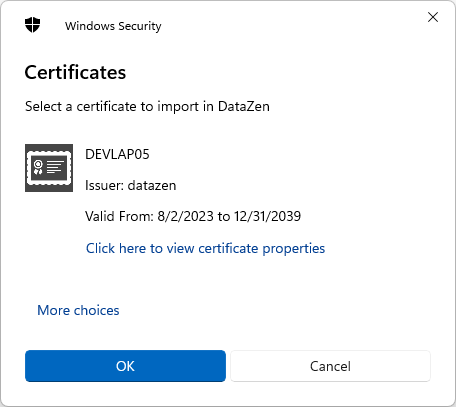
Import Certificate from Store
To import an existing certificate from the Windows Local Machine or User MY store,
choose New -> Import from Certificate Store and pick your certificate.
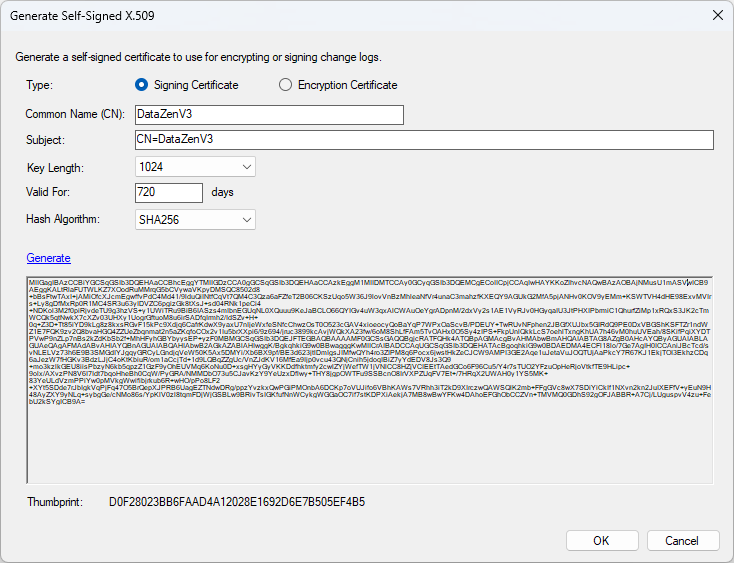
Self-Signed Certs
DataZen allows you to create self-signed certificates directly for encryption or signature. To create a new self-signed certificate,
choose New -> Generate Self-Signed Certificate, then choose the desired options for key length.
X.509 Certificates for DataZen Agent Authentication
DataZen agents support client authentication using an X.509 certificate. To use this option from PowerShell scripts or HTTP clients, add a https-Client-Certificate HTTP Header with the certificate thumbprint to use. In addition, the X-API-DateTime and X-API-DateTimeHash HTTP Headers must also be provided (see the X.509 used for signature section below).
Self-hosted agents always allow NTLM authentication unless the Authorization header is present.
If the anonymous flag is set for the agent, X.509 based authentication is ignored.
To use this feature, the following conditions must be met:
- The certificate must be registered with the agent as shown above and have a Digital Signature Key Extension
- The agent must be configured to allow authentication using the desired X.509 certificates
- The certificate must be installed with its Private Key in the local My Certificate Store (either in the Current User or Local Machine store)
- The connection to the agent must be modified to specify the use of this certificate for authentication purposes
X.509 Certificates for DataZen Agent Connection Signature
DataZen agents support signing connection requests with an X.509 certificate. This option is used alongside the Token authentication option to add an additional level of security to ensure client machines are authorized for access.
Choosing an X.509 signing mechanism requires all Token-based connections to be signed.
The following HTTP headers must be provided:
- https-Client-Certificate: The thumbprint of the X.509 signing certificate to use
- X-API-DateTime: The current timestamp in UTC using an ISO 8601 format; the date provided must be within 5 minutes of the current time on the server where the agent is running
- X-API-DateTimeHash: The base64 string representation of the signature of the date provided using the X.509 certificate, using a SHA1 algorithm; signing requires the private key of the certificate
Self-hosted agents always allow NTLM authentication to its API.
If the anonymous flag is set for the agent, signature headers are ignored.
To use this feature, the following conditions must be met:
- The certificate must be registered with the agent as shown above and have a Digital Signature Key Extension
- The agent must be configured to require signature from the desired X.509 certificates
- The certificate must be installed with its Private Key in the local My Certificate Store (either in the Current User or Local Machine store)